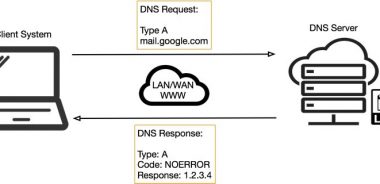
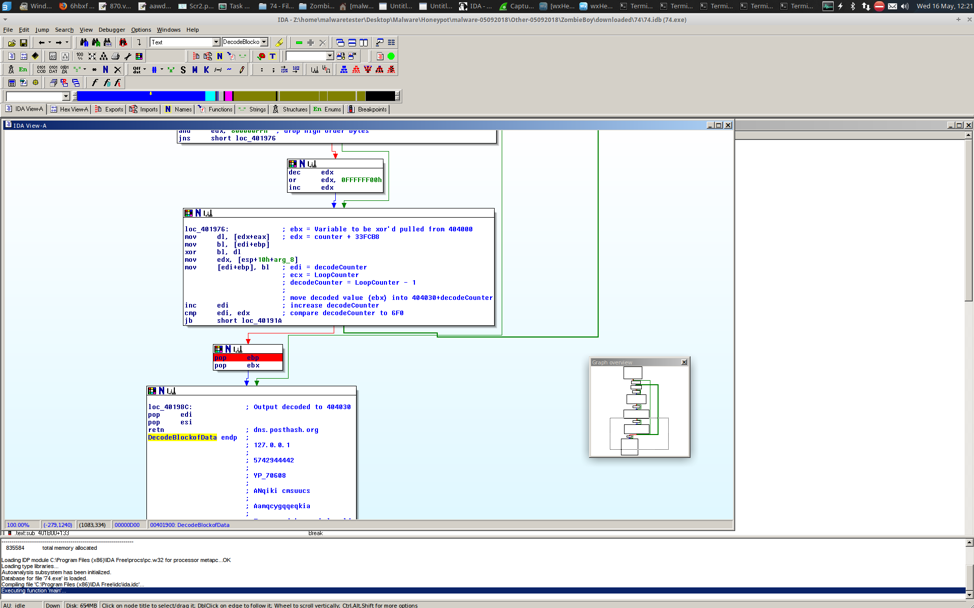
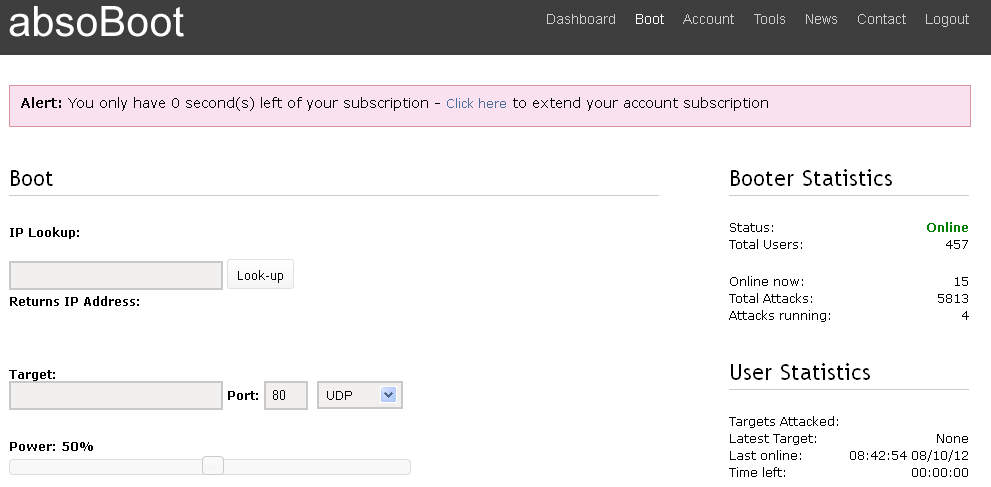
Abnormal Behavior Detection to Identify Infected Systems Using the APChain Algorithm and Behavioral Profiling
GitHub - AHXR/ghost: RAT (Remote Access Trojan) - Silent Botnet - Full Remote Command-Line Access - Download & Execute Programs - Spread Virus' & Malware